
A new malware has been identified, connected to Redline and disguising itself as a game cheat called ‘Cheat Lab.’ The creators entice users with a free download if they can persuade their friends to install it as well.
Redline is a powerful program designed to steal sensitive information from compromised computers. It is capable of obtaining passwords, cookies, autofill information, and even cryptocurrency wallet data.
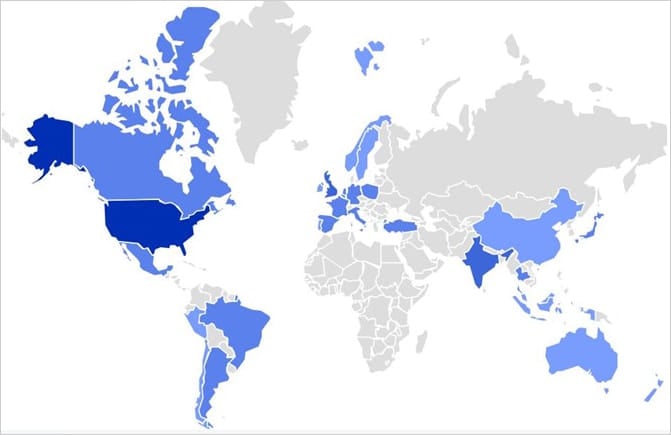
This malware is highly sought after by cybercriminals and is distributed globally through various channels.
(McAfee)
Experts at McAfee revealed that this new information stealer uses Lua bytecode to avoid detection. This enables the malware to inject itself into legitimate processes, operate undercover, and utilize Just-In-Time (JIT) compilation for optimal performance.
The researchers have linked this variant to Redline due to its use of the same command and control server previously associated with the malware.
However, BleepingComputer conducted tests and found that this particular malware does not exhibit all the traditional behaviors of Redline. For instance, it does not save browser information, passwords, or cookies.
Social Infection: Spreading through Friends
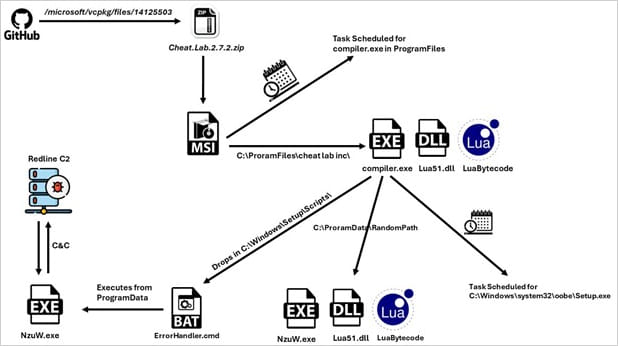
The malicious payloads of Redline are masquerading as demos of cheat tools named ”Cheat Lab” and “Cheater Pro.” These downloads are disguised as links to Microsoft’s ‘vcpkg’ GitHub repository.
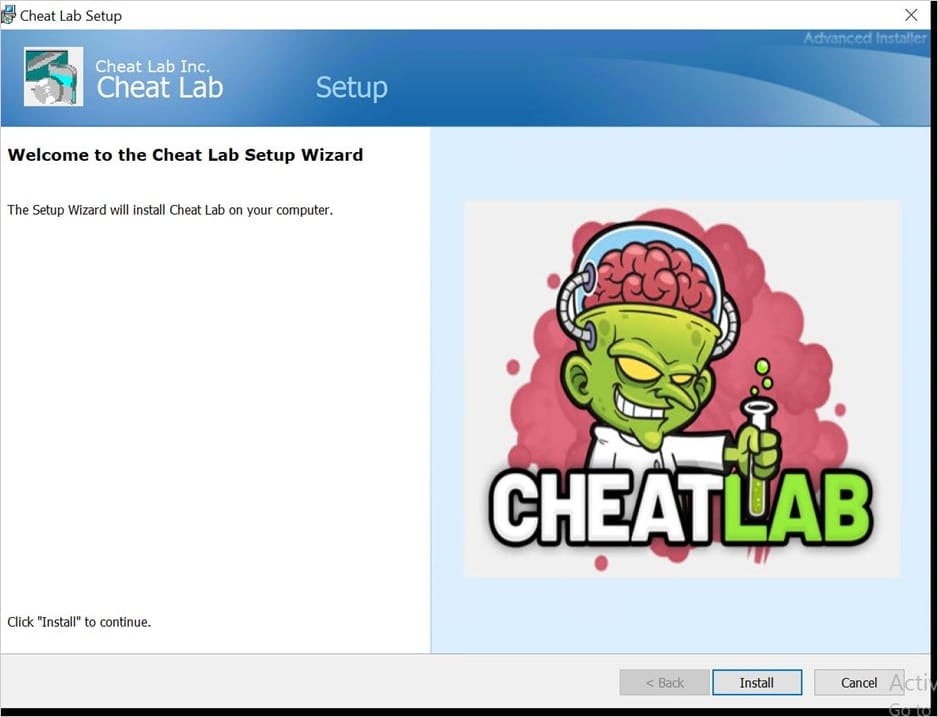
When users click on these links, they are directed to ZIP files that contain an MSI installer. Once launched, the installer unpacks two files, compiler.exe and lua51.dll. The package also drops a ‘readme.txt’ file containing the malicious Lua bytecode.
Source:McAfee
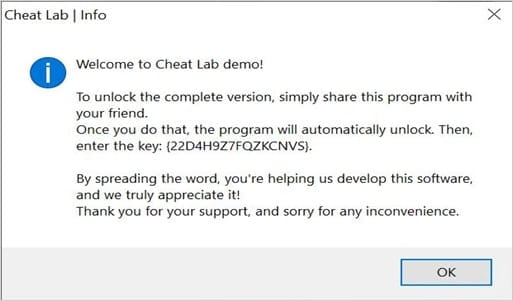
The creators of this campaign came up with an intriguing tactic to boost the spread of their malware. Users are promised a free, fully licensed copy of the cheating program if they can get their friends to install it as well. This approach also adds an activation key for added credibility.
“To unlock the complete version, simply share this program with your friend. Once you do that, the program will automatically unlock,” reads the installation prompt below.
Source:McAfee
In a clever attempt to go undetected, the malware is not distributed as a regular executable file. Instead, it is distributed in an uncompiled form as bytecode.
Upon installation, the compiler.exe file compiles the Lua bytecode stored in the readme.txt file and executes it. This same executable also sets up persistence by creating scheduled tasks that run during system startup.
McAfee researchers have also discovered a fallback mechanism for persistence, where the malware copies the three files to a random, lengthy path under program data.
Source:McAfee
Once activated on a system, the malware connects to a command and control server, sending screenshots of active windows and system information. It then waits for commands to execute on the compromised host.
The exact method of initial infection is still unknown, but information-stealing malware typically spreads through malvertising, misleading links in YouTube video descriptions, P2P downloads, and deceptive software download sites.
Experts advise users to avoid downloading unsigned executables and files from suspicious websites.
This attack serves as a reminder that even seemingly reliable platforms like Microsoft’s GitHub can harbor malicious software.
BleepingComputer reached out to Microsoft about the executables being distributed through its GitHub URLs, but has not yet received a response.
