
A recent scheme, dubbed “Dev Popper”, has been identified as a targeted attack against developers by offering fake job interviews and then tricking them into installing a Python remote access trojan (RAT).
In order to appear legitimate, the perpetrators have the developers complete tasks during the interview such as downloading and running code from GitHub.
This covert operation is aimed at getting the unwitting subjects to download malicious software that surreptitiously gathers system information and grants remote access to any infected devices.
The tactics observed in the “Dev Popper” campaign indicate that it is likely orchestrated by North Korean threat actors, although further evidence is needed to definitively attribute the attack. The connections to North Korea are based on their known tactics and techniques.
The intricate attack process
The attacks conducted by “Dev Popper” follow a complex multi-stage approach that utilizes social engineering to gradually compromise their targets.
The initial contact is made when the attackers pose as job recruiters searching for qualified software developers. During the interview process, the applicants are instructed to download and execute a coding task from a GitHub repository.
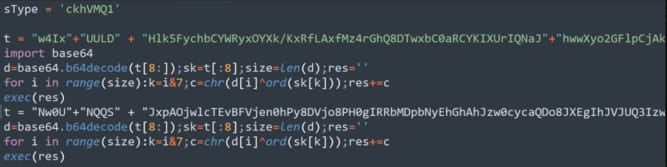
Concealed within the backend directory of the downloaded file is an NPM package that contains an obfuscated JavaScript file (“imageDetails.js”) which runs “curl” commands through the Node.js process to download an additional archive (“p.zi”) from an external server.

Securonix
Contained within the downloaded archive is the next stage payload, an obfuscated Python script (“npl”) that functions as a RAT.
Securonix
Once the RAT has been activated, it immediately begins collecting and transmitting basic system information to a command and control (C2) server. This includes information about the operating system, hostname, and network.
The RAT offers a range of malicious capabilities, including the ability to establish persistent connections for ongoing control, perform file system commands to search and steal specific files or data, remotely execute commands for further exploits or malware deployment, directly extract data from high-interest folders like “Documents” and “Downloads” via FTP, and log keystrokes and clipboard activity for potential credential theft.
While the perpetrators behind the “Dev Popper” attack remain unknown, this particular ploy of using fake job offers to distribute malware is still prevalent and serves as a warning for those in the software development community.
The researchers behind the investigation state that this method targets the trust and professional engagement of developers during the job application process, which makes it an effective tactic.
North Korean hackers have also been known to utilize fake job opportunities as a means to compromise their targets. In fact, last year there were multiple reports [1, 2, 3, 4, 5] of North Korean hacking groups using this tactic to target security researchers, media organizations, software developers (particularly those involved in DeFi platforms), and employees of aerospace companies.
In addition to the “fake job offer” method, North Korean threat actors have also been found to impersonate journalists in spear-phishing attacks aimed at extracting sensitive information from think tanks, research centers, and academic institutions.
