
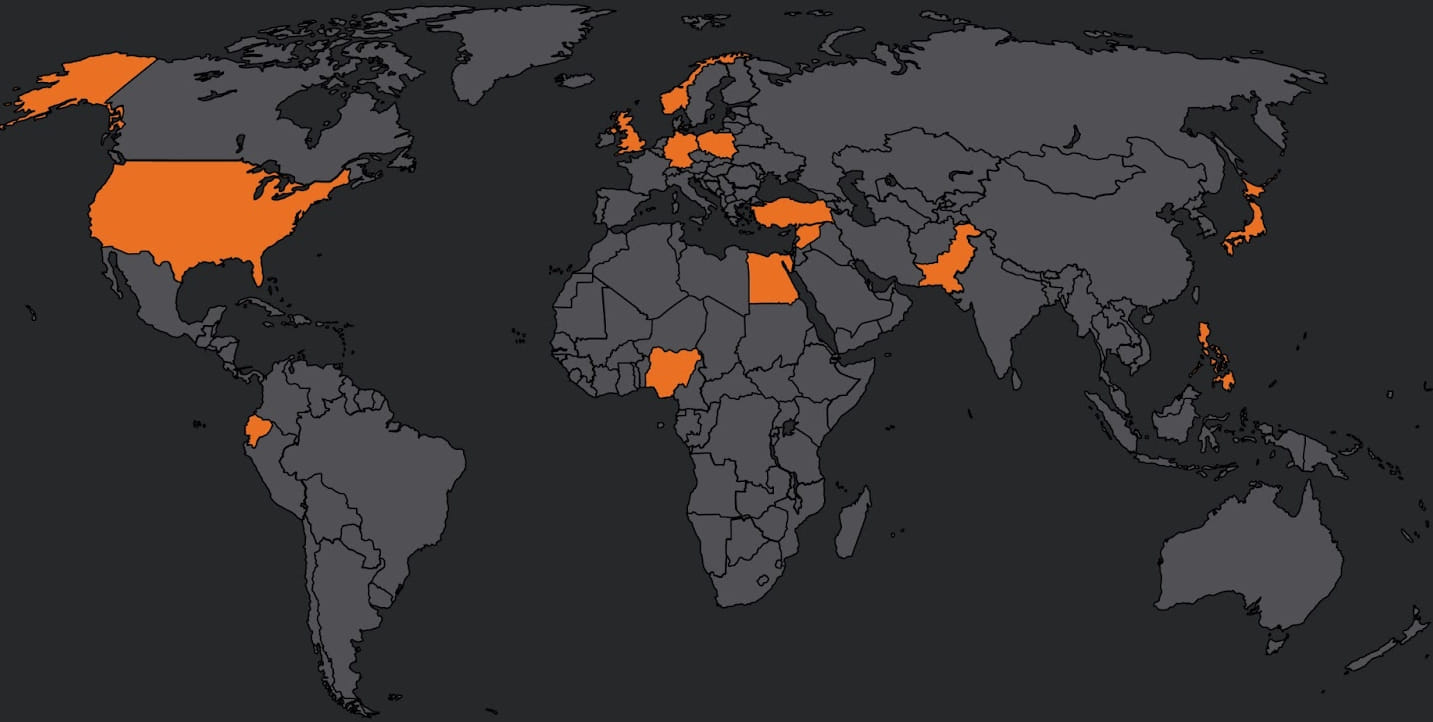
A malicious actor has been utilizing a content delivery network cache as a means to store confidential information-stealing malware as part of an ongoing campaign that specifically targets systems in the U.S., the U.K., Germany, and Japan.
It is suspected that the perpetrator behind these attacks is CoralRaider, an individual solely motivated by financial gains and who focuses on obtaining login credentials, financial data, and social media accounts.
The hackers are deploying a trio of information stealers, namely LummaC2, Rhadamanthys, and Cryptbot, which are all available on underground forums as malware-as-a-service platforms for a membership fee.
Cisco Talos has evaluated this campaign and has determined with moderate confidence that it is the work of CoralRaider, based on similar tactics, techniques, and procedures (TTPs) as past attacks attributed to this threat actor.
Signs pointing to CoralRaider include the initial methods of attack, the use of intermediate PowerShell scripts for decrypting and delivering the payload, as well as specific techniques to bypass User Access Controls (UAC) on the targeted machines.
Cisco Talos
CoralRaider’s route of infection
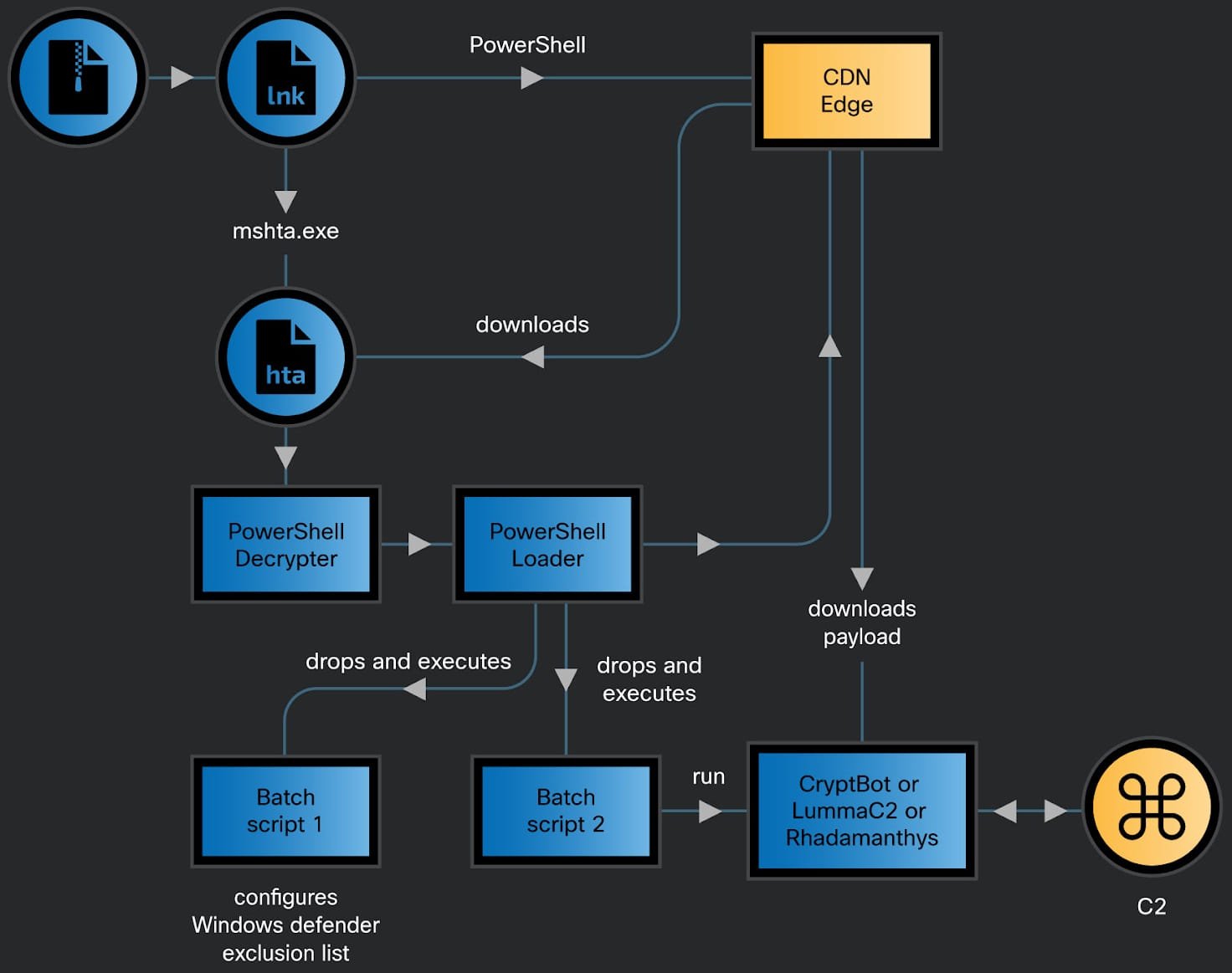
Cisco Talos has reported that their most recent CoralRaider attacks begin when the victim opens an archive that contains an unscrupulous Windows shortcut file (.LNK).
The delivery method of this archive remains unknown, but it could potentially be disguised as an email attachment, as a download from an unreliable source, or advertised through malicious advertisements.
The LNK file includes PowerShell commands that fetch and execute an extremely obfuscated HTML Application (HTA) file from a subdomain controlled by the perpetrator on the Bynny content delivery network (CDN) platform.
By making use of the CDN cache as a server for delivering malware, the threat actor can avoid any delays in requests and simultaneously deceive network defenses.
The HTA file comprises of JavaScript code that decodes and executes a PowerShell decrypter script, which then unzips a second script that generates a batch script in a temporary folder. The intention is to go unnoticed by altering the Windows Defender exclusions.
A native binary within the Windows system, known as FoDHelper.exe, is used to modify registry keys and bypass the security feature of User Access Control (UAC).
After this step, the PowerShell script fetches and executes one of the three information stealers (Cryptbot, LummaC2, or Rhadamanthys) that have been positioned in a specific location that is exempted from being scanned by Windows Defender.
Cisco Talos
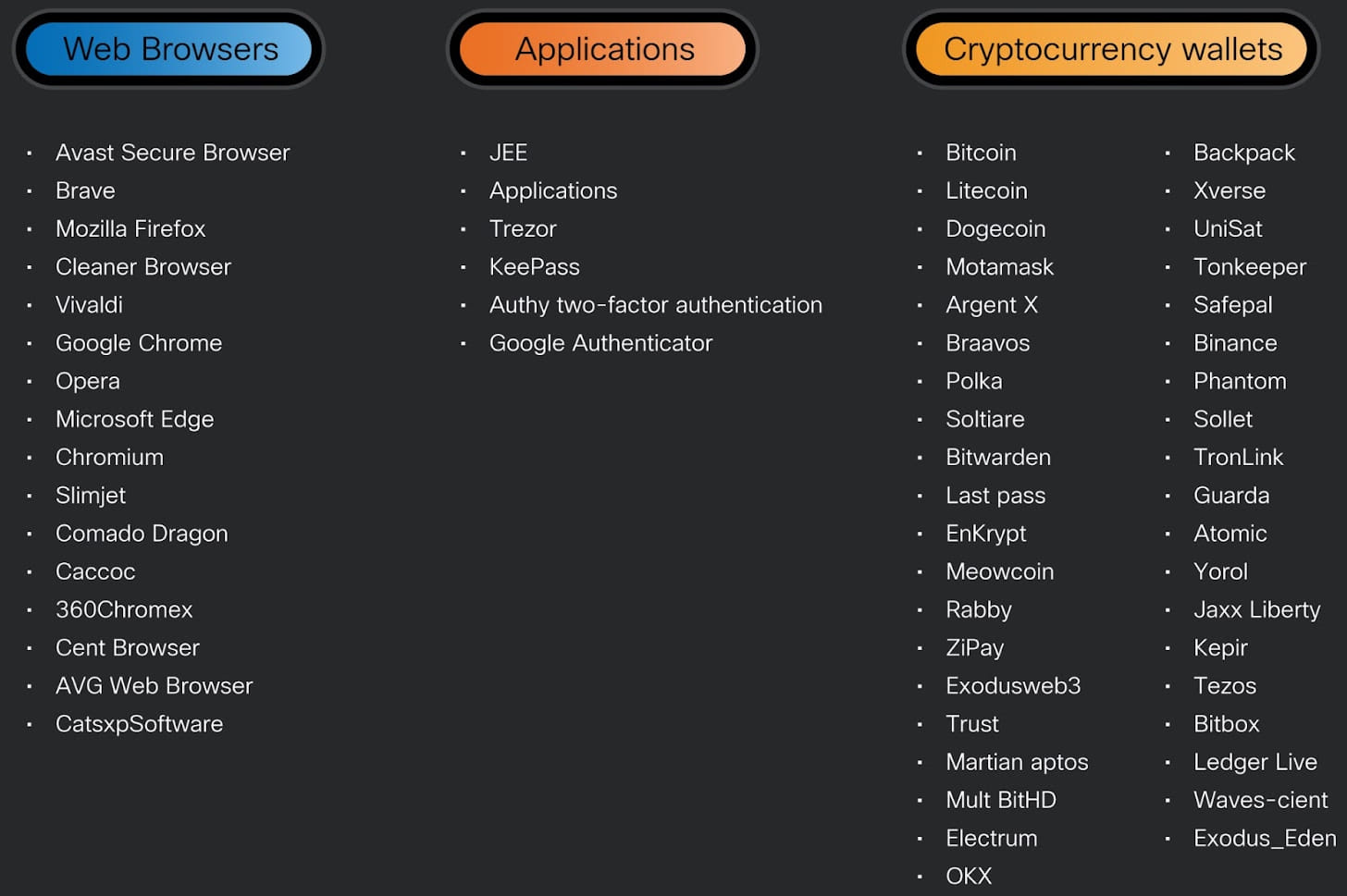
Types of information stolen
Cisco Talos reveals that CoralRaider has made use of up-to-date versions of LummaC2 and Rhadamanthys, which during the latter half of 2023 had incorporated advanced features such as capturing RDP logins and extracting expired Google account cookies [1, 2].
Even though Cryptbot is not as prevalent, it still poses a significant threat, infecting 670,000 machines within one year.
Cisco Talos points out that the version of Cryptbot witnessed in CoralRaider’s most recent attacks was introduced in January and is equipped with better obfuscation and anti-analysis mechanisms, as well as an expanded range of applications being targeted.
Cisco Talos
Cisco Talos also notes that in addition to databases for password managers, Cryptbot is also targeting authenticator app data to steal cryptocurrency wallets that are protected by two-factor authentication.
CoralRaider has been operational since at least 2023 and it is speculated that its base of operations is in Vietnam. In a previous campaign, the perpetrator had relied on a Telegram bot as a means of command-and-control (C2) and also to exfiltrate victim data.
The majority of its victims can be found in countries in Asia and Southeast Asia. However, the most recent attack has expanded its reach to countries like the U.S., Nigeria, Pakistan, Ecuador, Germany, Egypt, the U.K., Poland, the Philippines, Norway, Japan, Syria, and Turkey.
