Kubernetes Cryptomining Campaign Targets OpenMetadata Workloads
In a recent cyber attack, threat actors have been exploiting vulnerabilities in OpenMetadata to target Kubernetes workloads and install cryptomining malware.
OpenMetadata, an open-source metadata management platform, is widely used by data engineers and scientists to catalog and discover data assets within organizations. However, the platform has recently been targeted by attackers due to critical remote code execution and authentication vulnerabilities.
These vulnerabilities, including CVE-2024-28255, CVE-2024-28847, CVE-2024-28253, CVE-2024-28848, and CVE-2024-28254, were patched in March of this year, but many organizations have failed to update to the latest versions (1.2.4 and 1.3.1), leaving their workloads vulnerable.
The first to identify these attacks was Microsoft, who reported that the flaws have been actively exploited since April to take control of unpatched OpenMetadata workloads accessible on the internet.
According to threat intelligence researchers Hagai Ran Kestenberg and Yossi Weizman, the attackers begin by identifying vulnerable versions of the application and then exploit the vulnerabilities to gain remote code execution on the container running the OpenMetadata image. Once they have access, the attackers download a cryptomining-related malware from a remote server, which has been found to be located in China.
The server hosting the malware payloads also contains other cryptomining malware for both Linux and Windows platforms.
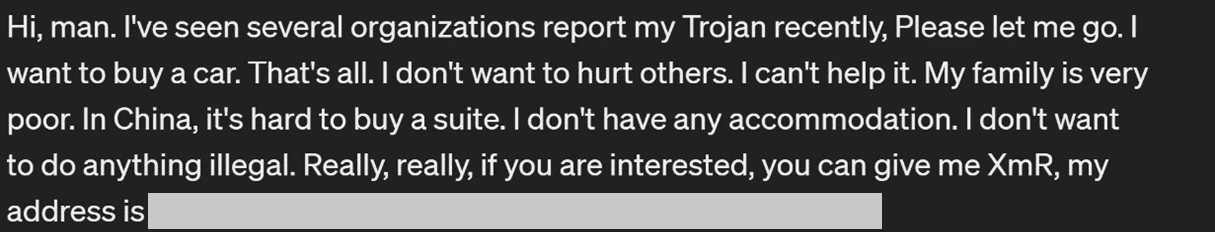
In addition to installing malware, the attackers also leave a note on compromised systems, requesting that the victim donate Monero cryptocurrency to help them buy a car or a “suite” in China.
Once they have established control of the system, the attackers then remove the initial payloads and create a reverse shell connection using the Netcat tool, allowing them to maintain remote access. To ensure persistent access, the attackers use cronjobs to schedule tasks that execute malicious code at predetermined intervals.
To protect against these attacks, it is crucial for administrators to change the default credentials and keep their OpenMetadata workloads up-to-date with the latest security patches.
If you are unsure if your organization is running vulnerable OpenMetadata workloads in a Kubernetes environment, you can use the following command to get a list of all workloads:
kubectl get pods --all-namespaces -o=jsonpath='{range .items[*]}{.spec.containers[*].image}{"n"}{end}' | grep 'openmetadata'
This attack highlights the importance of maintaining compliance and running fully patched workloads in containerized environments,” Kestenberg and Weizman concluded.
