
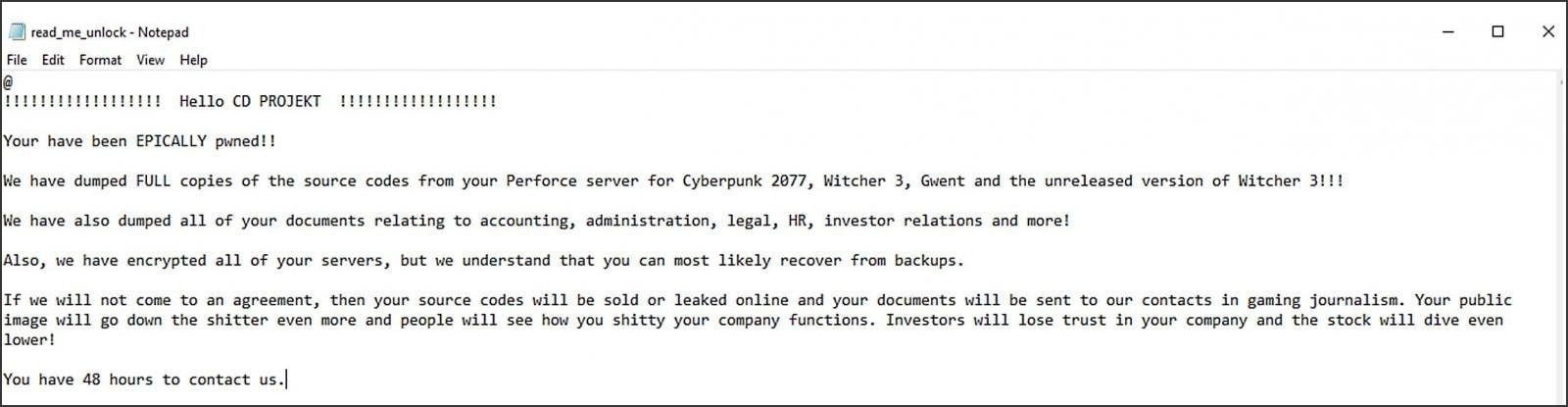
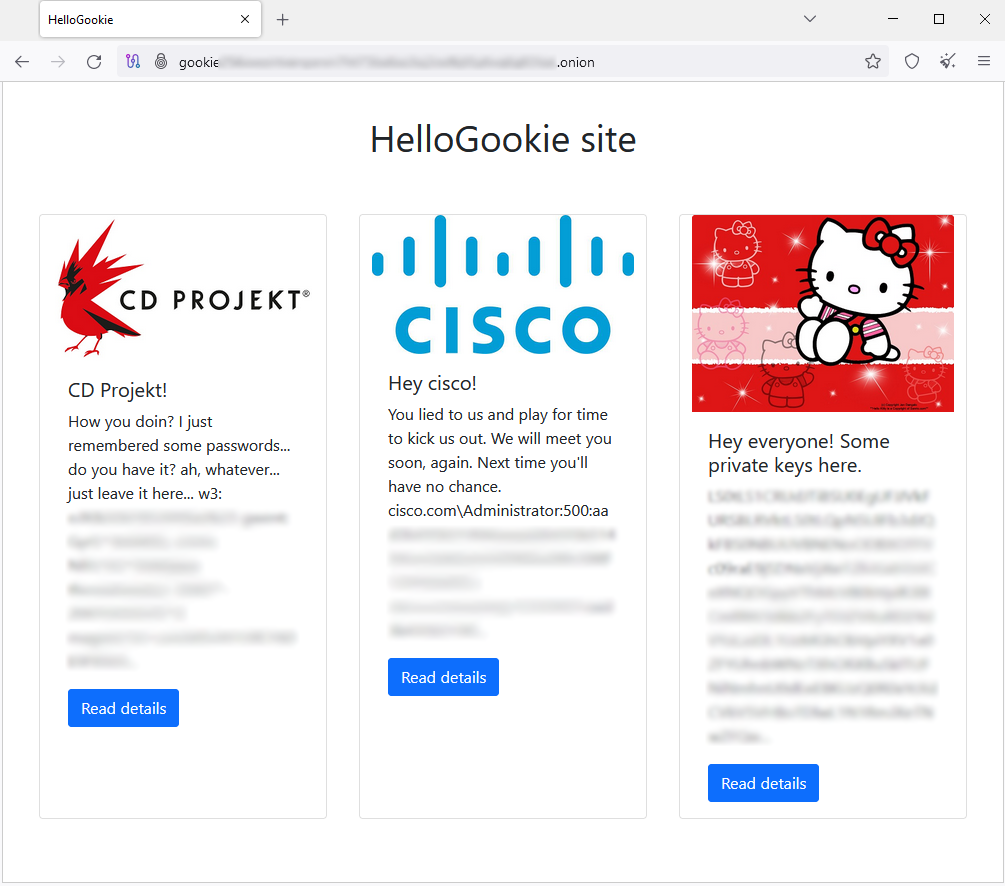
The operator of the HelloKitty ransomware operation recently revealed a new name, ‘HelloGookie,’ along with the release of passwords for previously leaked CD Projekt source code, Cisco network data, and decryption keys from past attacks.
The individual claiming responsibility for the rebrand goes by the moniker ‘Gookee/kapuchin0’ and purports to be the original creator of the now-defunct HelloKitty ransomware.
According to the first source of this information, threat researcher 3xp0rt, the rebrand coincides with the launch of a new dark web portal for HelloGookie.
In celebration of the launch, the threat actor also made four private decryption keys available for use, allowing victims of older attacks to recover their encrypted files. Additionally, passwords for leaked source code for Gwent, Witcher 3, and Red Engine, all stolen from CD Projekt in 2021, and internal information taken during a 2022 attack against Cisco, were also released.
The team at VX-Underground, a group of developers, were the first to discover that individuals had successfully compiled Witcher 3 from the leaked source code. Screenshots and videos of development builds have since been shared by the group.
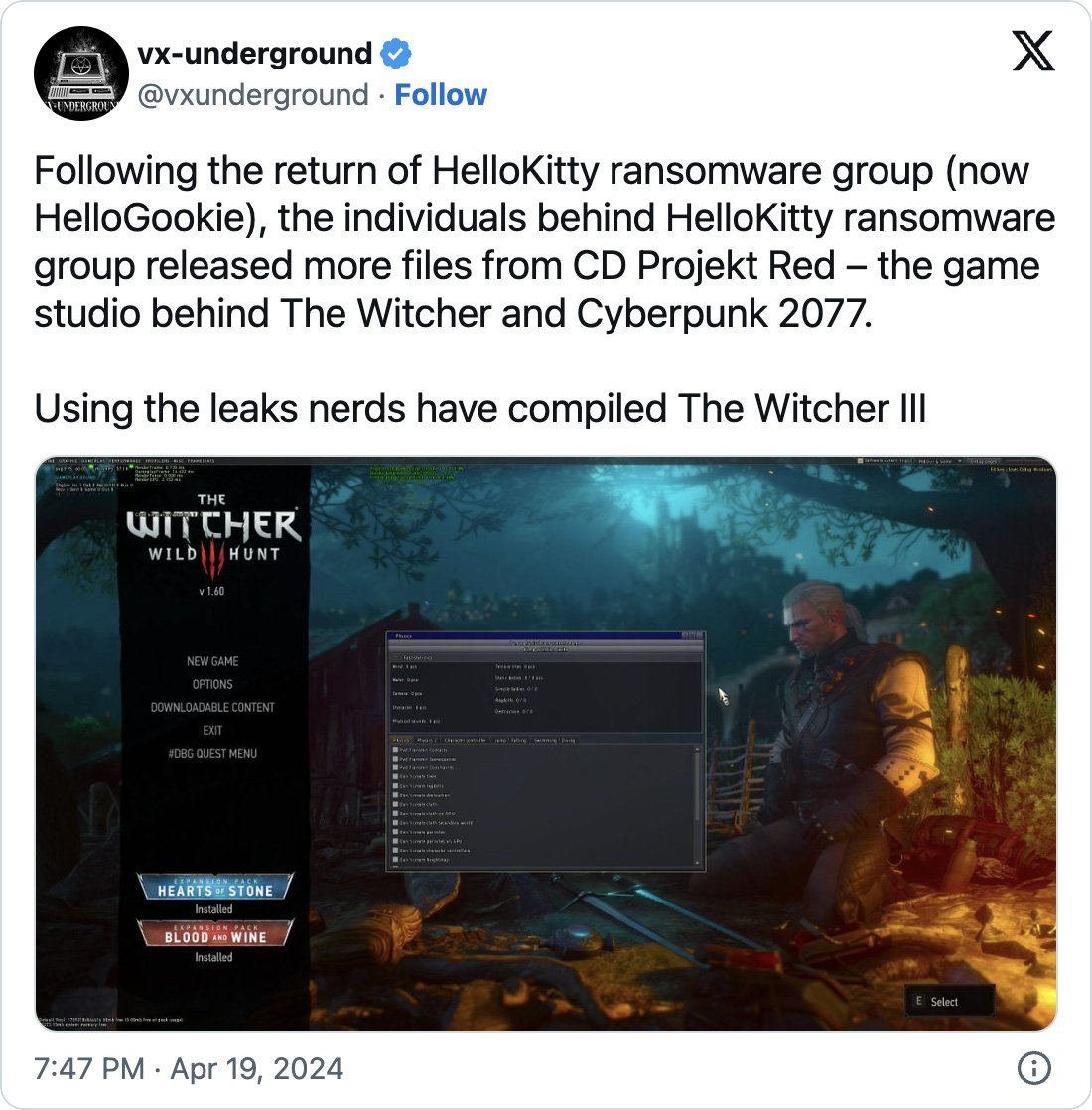
One of the developers involved in compiling Witcher 3, known as ‘sventek’, told BleepingComputer that the leaked CD Projekt data is 450 GB when uncompressed and contains the source code for Witcher 3, Gwent, Cyberpunk, various console SDKs (PS4/PS5 XBOX NINTENDO), and build logs.
BleepingComputer was also able to confirm that the leaked source code contains binaries that can be used to launch a developer build of Witcher 3. The developers shared a video and screenshots with BleepingComputer that were taken from an early build.
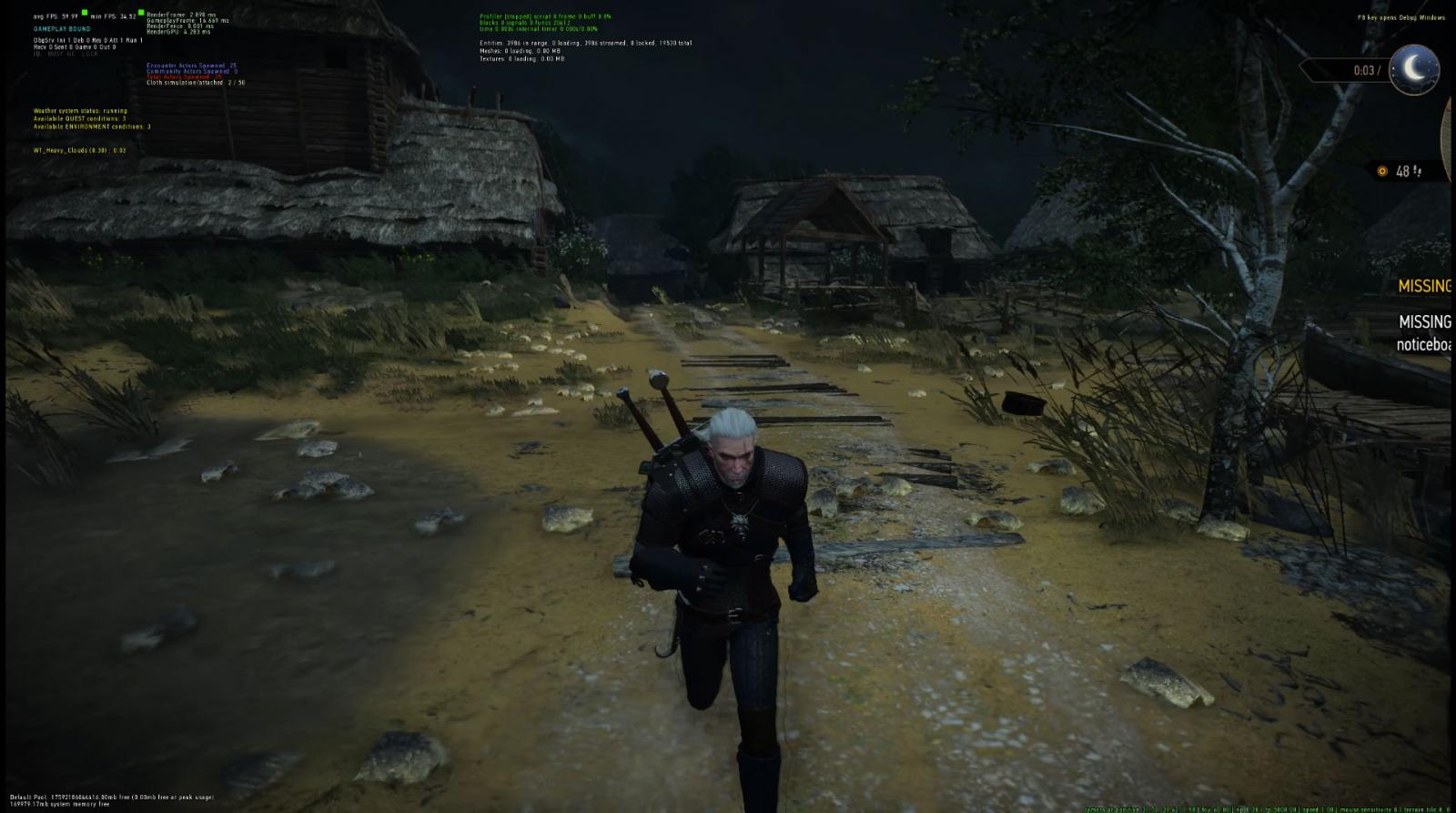
Source: Sventek
Sventek also shared that they have previously managed to compile Cyberpunk 2077 from the CD Projekt leak and were behind the previous GTA V source code leak.
The Origins of HelloKitty
HelloKitty first emerged as a ransomware operation in November 2020, known for targeting corporate networks, stealing data, and encrypting systems.
The group gained notoriety after their first high-profile attack in February 2021, where they breached CD Projekt Red, the company behind Cyberpunk 2077, Witcher 3, and Gwent. During the attack, the ransomware gang encrypted the company’s servers and stole source code.
Source: BleepingComputer
HelloKitty went on to claim that they had sold the stolen data on the dark web, including the code for the then-unreleased Witcher 3.
The HelloKitty ransomware operation continued to grow in 2021 when they released a variant focused on targeting Linux systems, specifically VMware ESXi. The addition of this variant created more opportunities for the group to profit from their attacks.
In 2022, conversations between members of the Yanluowang ransomware group, had their data leak site hacked and the conversations revealed a strong connection between them and the developer of HelloKitty, who was using the alias Guki.
Later in October of 2023, Gookee/kapuchin0 leaked the HelloKitty builder and source code on a hacker forum, signaling the end of the operation.
HelloGookie Emerges
The threat actor has recently announced that they have rebranded the operation as HelloGookie, although there is no evidence of recent attacks or victims attributed to this new name.
Despite the lack of current activity, the threat actor did release stolen information from previous attacks on CD Projekt Red and Cisco. The data leak site now also includes four private decryption keys for an older version of the HelloKitty ransomware, allowing some victims to potentially recover their files for free.
Researchers at BleepingComputer are currently investigating the keys to determine which versions of the encryptor they are compatible with.
BleepingComputer
The data leak for Cisco contains a list of NTLM (NT LAN Manager) hashes, which are encrypted account passwords that were supposedly extracted during a security breach. In 2022, Cisco admitted to being hacked by the Yanluowang ransomware group, but stated that the incident was limited to the theft of non-sensitive data from a single compromised account.
However, the fact that this information was accessible to kapuchin0 and that they gave a shout-out to Yanluowang suggests a closer relationship between the two groups than previously known.
“Cisco is aware of the recently published information referencing a security incident in May 2022. A detailed summary of the incident can be found in this August 2022 blog post by Cisco Talos, our threat intelligence research organization,” Cisco told BleepingComputer in response to the data leak.
It remains to be seen whether HelloGookie will be able to replicate the success, attack volumes, and notoriety of its predecessor, HelloKitty.
